How Blockchain Is Enhancing Cybersecurity and Transparency
We are inundated with data in the digital world of today. Our personal information, financial records, health records, supply-chain logs, and identity credentials are the sources. Along with this abundance comes danger: data breaches, tampering, fraud, opaque systems, and insider threats. Traditional, centralized systems have been the solution for us up till now, but they mostly result in trust bottlenecks and single points of failure.
What if a system that endorsed integrity, allowed group verification, was resistant to tampering, and made hidden operations visible, were there instead of a single gatekeeper whom you trusted to manage and protect your data? This is the point at which blockchain makes its entry not only as the structure that supports cryptocurrencies but also as a revolutionary instrument to cybersecurity and digital ecosystem transparency improvement.
We will learn how these characteristics, decentralization, immutability, cryptographic security, and transparency, that define blockchain technology, help in security issues that are persistent in this blog. Furthermore, we shall consider practical implementations, be vigilant of potential pitfalls, and glimpse into the possible future.
The Foundations: What Makes Blockchain Special
Before going deeper into the range of applications, it is always a good idea to have a look at the factors that make the blockchain very special.
1. Decentralization/Distributed Ledger:
Unlike in a central server, the data of a blockchain system is not the same. Several copies of the ledger (the chain of blocks) are distributed across nodes (computers). That is the reason why there is no point of failure, in the case of a cyber-attack, to rewrite the record.2. Immutability / Tamper-resistance:
The retroactive change of one block, which was appended and accepted through consensus, would mean someone has to modify all the blocks that come after it and also get the majority of the nodes' approval. This is almost impossible from a computational and an economic standpoint if it is a well-designed system.3. Cryptographic Security & Hashing:
Hashes are used to represent data entries (or transactions), and each block contains the hash of the previous one. Therefore, these blocks are linked, and in case a block has been changed, the chain will stop being linked. In addition, the combination of public and private keys for encryption adds a security layer, as only those who have the required authority to sign or decrypt certain data can perform these actions.4. Transparency/Auditability:
Whether blockchains are public or permissioned, but are auditable, and the entire history of the chain of operations is visible to the participants. Every transaction is recorded, time-stamped, and is viewable (depending on permission) in a manner that cannot be quietly hidden.5. Smart Contracts/Programmable Logic:
These are on-chain, permanently stored, self-executing code fragments that implement the agreed actions once the specified conditions have been met. On top of technology errors being less likely, the smart contracts can also be used to instill security policies or rules.
It is noteworthy that the new model of security is not something that is added later, but the very architecture itself, which is security by design, and each of these features, when integrated.
Why We Need Better Cybersecurity & Transparency

To see the value of blockchain, one has to understand the problems first.
Single points of failure/centralization:
Most traditional systems are essentially centralized in either their server or administrative personnel. If the component in question is compromised, fails, or turns out to be of ill intent, then everything is at stake.Data tampering & lack of trust:
If logs, audit trails, or records are saved in a centralized manner, they can be changed, deleted or forged. This results in a decrease in the trust level between all the stakeholders, especially in the case when the number of parties is involved (e.g., supply chain, audits, multiple vendors).Opaque processes / limited visibility:
Most systems conceal the way they operate internally. Users or regulators need to believe what service providers say (e.g., “we blocked this attack,” “we conform to these standards”). Without being able to verify the claims, it is sometimes difficult to accept them as true.Siloed threat intelligence:
Many organizations gather and keep secret the data of threats directed at them. It is difficult to share it in a secure way because of issues with trust, privacy, and attribution.Identity and access vulnerabilities:
In a situation where the central identity repositories suffer a security breach, they will be the first targeted places by the attackers. At that point, the hijackers may even pretend to be other users, increase their access levels, or just use the credentials.Regulatory and compliance pressures:
Regulations (such as GDPR, HIPAA, PCI-DSS) require organizations to provide proof of compliance, traceability, and accountability.. However, centralized logging and auditing systems can be compromised without the external appearance of tampering.
Blockchain technology can ease the impact or completely change the way the problems mentioned above are solved.
How Blockchain Elevates Cybersecurity & Transparency
The advantages of distributed ledger technology are as follows:
1. Non-Relocatable Traceability And Reconstruction
Since all transactions are documented, timestamped, and linked to other related entries via a ledger that is tamper-evident, the audit trails hold true now. If one suspects manipulation of data, identification of the offender, along with the exact time of operatio,n can be done without depending on a central log that may have been modified.
2. Decentralized Threat Intelligence Sharing:
One of the instances of a good idea that has a benefit is decentralized threat intelligence shared by multiple organizations (governments, enterprises, security vendors) that provides on a blockchain such data as attack signatures, malicious IPs, anomalies, and discoveries. Since all input is verifiable, trusted, and timestamped, the difficulty of a single bad actor altering or injecting false data without being found is high.
This practice is fostering co-defense: the threats that one spots can be immediately and safely sent to the rest without the need for a central authority to carry out the supervision.
3. Identity, Authentication & Access Control:
Blockchain technology has the ability to improve the identity management system from which the secure decentralized identity (DID) is derived. Users or devices have identity-related credentials that are stored (hashed) on-chain rather than with a central identity provider. When a person proves an identity, he/she give verifiable cryptographic proof.
Besides that, projects like ChainGuard present blockchain-based authentication and access control where the user roles and permissions managed by a central server are replaced.
Thus, the risk of a hacked centralized identity store that could lead to widespread impersonation or insider fraud is reduced.
4. Secure IoT & Device Integrity:
The Internet of Things (IoT) is known for its lack of security due to small gadgets being located in remote areas, and challenging to keep up to date. Blockchain might be able to support it in the following ways:
Making device firmware updates or configurations as transactions so that they can be tamper-evident.
Utilizing smart contracts to establish the validity of the device communication that complies with the set rules.
Identifying the record of the device that was the closest to the network unit and was the one that interacted with it at the time.
Therefore, you are limiting the possibility that a hacker has changed the firmware without your knowledge or pretending to be a real device.
Actually, they are creating blockchain-based platforms for the certification status of IoT devices (under regulation) to provide a security status that is visible to everyone.
5. Supply Chain Transparency & Anti-Fraud:
Although supply chain security is not entirely a “cyberattack” issue, it is still a big concern. Counterfeit goods, tampered parts, unauthorized substitutions - these not only rob trust but also create security risks (e.g., malicious chips). Blockchain technology offers complete traceability: the history of every part is available, and it can be checked where, when, and by whom the change was made, and even be inspected for purity at any time during the process.
For instance, a pharmaceutical company can monitor batches, shipments, and ownership, thus allowing the recipient to verify that the route has not been tampered with.
6. Transparent Vendor Claims / Security Assurance:
In the cybersecurity vendor market, companies tend to make claims (“we detect 99.9% of all threats,” “we stopped X attacks,” etc.). However, the customers have to take these claims at face value. Blockchain links these claims to the actual records, such as logs of attack signatures, blocked events, and false positives, which are auditable and cannot be altered. This transforms claims into a verifiable form.
Hence, the vendor is not allowed to negate or alter the past performance later; customers can check it on-chain themselves.
7. Regulatory Compliance & Auditability:
Absolutely, blockchain has very strong audit trails and guarantees of immutability, thus regulators and auditors can always pinpoint the location of the records. By utilizing blockchain, organizations that have to deal with compliance issues (healthcare, finance, and industries critical for infrastructure) can very easily prove that they have complied with the requirements.
In some regions, cybersecurity laws are very hard on failures organizations can use blockchain-supported logs as evidence to show that they have taken all the necessary steps.
Real-World Examples & Illustrations
Instead, we could better connect those concepts to actual or mock usage cases:
Cybersecurity as a service + threat logs:
One example is some blockchain-based security platforms that record the attack/defense metadata (IP addresses, hashes of malicious payloads, etc.) on-chain. The clients are thus allowed to verify if an attack is not a fabrication, how the issue was resolved, and if the vendor gives the value as promised.IoT device certification:
This has also been mentioned as an idea to publish the device status of IoT certification on the blockchain. They can transmit their security credentials, firmware versions, etc. Devices, network managers, or users can verify the up-to-dateness of the devices in such a way.Supply chain traceability (e.g., OpenSC):
OpenSC is a platform that utilizes blockchain technology to track the movement of physical goods through supply chains. The initial idea of the project is centered on sustainability and the ethical sourcing of supplies; the same transparency can be used to detect fraudulent substitutions or hiding of tampering.ChainGuard (decentralized access control):
One such concept is that of employing smart contracts to govern the user roles and access rights in distributed systems that do not have centralized auth servers; thus, the dependence on such servers is completely abolished.Industry Cyber-Physical Systems (ICPS):
Scientists have proposed the use of blockchain technology to store the control commands, state changes, sensor data, etc., for the case of vital infrastructure (power grids, manufacturing plants) so that any malicious alterations could be easily spotted.
These examples show how versatile blockchain technology is in the different areas of use: from software and network security to physical systems and supply chains.
Challenges & Limitations to Be Mindful Of

It is essential to notice that although blockchain tech may be solid and effective, it is not a wonderworking solution to all the issues of the market. Its shortcomings, as well as tokens, need to be considered before a blockchain trip is planned.
1. Scalability & Throughput:
The majority of blockchains, in particular, the public ones, have the issue of low transaction speeds and high latency. As an example, a delay in a live security system would cause a lot of disappointment.
The problems, however, could be mitigated to a certain degree by implementing sharding, layer-2 / off-chain transactions, or permissioned blockchains.
2. Privacy vs Transparency Tension:
Since they are, by definition, public ledgers, being natural, they are quite suitable for the audit process; nevertheless, there are certain exceptions, i.e., healthcare data, where the sharing of the individual's data is the last thing one would want to do. The use of zero-knowledge proofs (ZKP), selective disclosure, and permissioned blockchains could be found in most cases of such debates.
3. Smart Contract Vulnerabilities:
Smart contracts are basically computer programs whose errors or vulnerabilities in the code may be exploited by hackers for their own benefit (e.g., reentrancy attacks). The process of comprehensive testing together with formal verifications is very important when human lives and large amounts of money are involved, thus these smart contracts are heavily used in security sectors.
4. 51% Attacks & Consensus Manipulation:
Imagine a situation with an insufficient number of nodes or their improper distribution, a villaintaking over the majority of computing power (or stake) would have the power to alter the ledger very quickly. The risk of such an event happening in big and well-distributed blockchains is slight, but small, customized networks still have to be cautious.
5. Interoperability & Integration Complexity:
The current non-blockchain system architecture. Sometimes the incorporation of blockchain with present IT stacks, databases, and applications may become problematic, expensive, and inefficient.
6. Regulation, Governance & Legal Ambiguity:
Once a piece of information has been stored on the blockchain, it cannot be altered or removed - quite a frightening feature if there ever was a requirement to delete data (e.g., by the "right to be forgotten" regulations). Moreover, the regulatory frameworks for blockchain, which can be found worldwide, are still fairly new.
7. Energy & Cost:
For instance, one of the heavily energy-consumption criticized consensus mechanisms is the proof-of-work method.
Moreover, the blockchain architecture (nodes, storage, consensus) could still be a large energy consumer and have high operational costs.
It is for this reason that some real-life applications of blockchain are often run as hybrid or permissioned / consortium blockchains (participants are known) rather than as fully open and public ones.
How Organizations Can Get Started: A Practical Roadmap
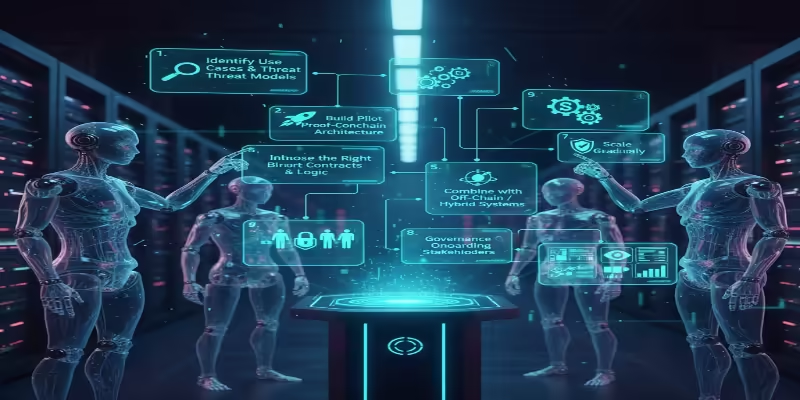
If you recognize the potential of the blockchain in addressing security and where the data is transparent, this is a very rough route towards the technology's adoption:
1. Identify Use Cases & Threat Models:
Begin by finding examples in which a company works with the issues of confidence, inspectability, or the chance of being altered. Internal logs, vendor claims, device firmware tracking, identity systems, or supply Chain data are some examples of such cases.
2. Build Pilot / Proof-of-Concept (PoC):
Don't post-reinvent the entire system. Just get started with a small one. For example, event logs (login attempts, admin actions) can be recorded on a permissioned blockchain.
3. Choose the Right Blockchain Architecture:It basically boils down to whether you want a permissioned, consortium, or public chain, the method of arriving at consensus, and the handling of the privacy part.
4. Integrate Smart Contracts & Logic:
Convert the business/security rules into smart contract format (e.g. "only certified firmware versions are allowed," or "only authorized users can approve changes of the key").
5. Combine with Off-Chain / Hybrid Systems:
Off-chain storage or sidechains may carry the burden of heavy data, while the integrity (through hashes) is on-chain.
6. Audit, Test & Harden:
Software auditing, pen-testing, and scenario simulation. You should be prepared for the edge cases, rollback, and failure situations.
7. Governance & Onboarding Stakeholders:
In a multi-party setup, you have to define the roles, permissions, dispute resolution, and upgrade paths. Framing partners, auditors, and regulators is a way to get them on board.
8. Scale Gradually:
After you turn into a system with great robustness and efficiency, continue the logs for use in identity systems, supply-chain tracking, threat intel sharing, etc.
9. Monitor & Maintain:
Blockchain nodes, consensus health, synchronization, forks, upgrades, and patches all need continuous operations to provide the service.
Looking Ahead: What the Future Holds
Basically, Blockchain, What some Trends and Things to Consider are to be the Most Impacting Points of the Future of Blockchain Security and Transparency Are Maybe the Following:
Integration with AI / ML:
Use machine learning to detect anomalies and let the system write the alerts or model changes directly on the chain. Combine predictive alerts with unchangeable logs.Decentralized Autonomous Security Agents:
Self-regulated security policy smart contracts, that automatically adjust the safety measures, answer the security challenges, or cancel access rights as per the changes in the on-chain.Privacy-preserving Techniques:
One of the major trends in privacy protection technologies will be the use of zero-knowledge proofs, secure multiparty computation, confidential computing, and homomorphic encryption. These methods will be used more and more to achieve privacy of data as well as its verification at the same time.Standardization & Interoperability:New and better protocols for cross-chain data sharing, identity portability, and audit frameworks across blockchains are the main features of the implementation.
Blockchain + Confidential Computing:
To the core, confidential computing involves keeping data safe while it is being used, so when combined with blockchain (which ensures the safety of data at rest and during transit), the final result is security at every stage. However, it is still a developing niche.Regulatory & Legal Maturation:
We may anticipate a clearer set of rules about data protection, liability, evidence law, etc. associated with blockchains as governments become more conversant.Ubiquitous Supply Chain / Logistics Tracking:
Nothing from microchips to pharmaceuticals and food would be without a blockchain-backed verifiable provenance. Eventually, transparency will be the standard instead of an exception.
Conclusion
Blockchain definitely doesn't solve every security problem instantly; however, it still provides an interesting base that significantly changes the presuppositions we use. Instead of having to rely on a single authority that is in charge of logs, records, identities, or device firmware, we can have systems where the very infrastructure guarantees the rights, the visibility, and the accountability.
Trust-deficit-ridden organizations facing auditing difficulties or opaque relationships with vendors can find in blockchain a way of getting verifiable assurance, collective defense, and tamper-proof proof. With the rise of technology and solid privacy strategies in hybrid models, we might witness a crypto-blockchain-mainstream cybersecurity trend rather than a niche one.
If you want, I could also assist you in creating visuals, a slide deck for this blog, or a shorter version of the blog just let me know.